At the latest Infobip Shift Conference in Zadar, I attended a fascinating presentation on passkeys – the new standard for passwordless login. This technology, also known as FIDO authentication, is gaining momentum, with major platforms like Google, Apple, and Microsoft adopting these passwordless authentication methods. While discussing this topic, I’ve noticed that many people have heard of passkeys but don’t fully understand how they work. In this blog, I’ll break down the concept of passkeys and passwordless authentication to explain both their current state and future implications.
Your Dog’s Name and Birth Year Aren’t Exactly Fort Knox 🐾🎂
Passwords have become one of the biggest security vulnerabilities in our digital lives. They’re difficult to remember, easy to steal, and increasingly vulnerable to sophisticated attacks. This creates a significant cybersecurity challenge for both individuals and organizations.
The problem is multifaceted. Users often choose weak passwords that are easy to remember, reuse the same passwords across multiple accounts, or store them in unsafe ways. Even when following best practices, passwords can be compromised through data breaches, phishing attacks, or malware.

According to Verizon, 81% of hacking-related breaches are caused by weak or stolen passwords. Recent data from SlashNext shows a staggering 1,265% increase in malicious phishing emails since Q4 2022, with credential phishing specifically rising by 967%. The FIDO Alliance reports that 54% of consumers have noticed phishing messages becoming more sophisticated in the last 60 days. – Source
The statistics above paint a clear picture: passwords are at the heart of most security breaches. With an alarming rise in phishing attacks and increasingly sophisticated social engineering techniques, traditional password-based authentication is becoming more vulnerable than ever.
Moreover, managing passwords has become increasingly complex. The average person needs to remember dozens of passwords for various services, leading to “password fatigue” – a situation where users compromise security for convenience by using simple, repeated passwords or writing them down in unsafe locations.
Password-Free Living: What’s That All About? ✨
Passwordless authentication is a modern security method that eliminates the need for traditional passwords. Instead of requiring users to remember and enter complex strings of characters, this approach uses alternative verification methods such as biometric data (fingerprints, facial recognition), security keys, or cryptographic credentials stored on your devices.
The core principle behind passwordless authentication is proving your identity through something you have (like your phone or security key) or something you are (your biometric data), rather than something you know (a password). This method is not only more convenient but also significantly more secure than traditional passwords, which can be forgotten, stolen, or compromised.
For example, when you unlock your smartphone with your fingerprint or face, you’re using a form of passwordless authentication. Similarly, when you receive a one-time code via SMS or email to log into an account, that’s another type of passwordless verification, though not as secure as modern passkey solutions.
Meet Passkeys: Your VIP Pass to Easy Login 🎟️
Passkeys are the next evolution in passwordless authentication, offering a more secure and user-friendly way to access your accounts. They work by creating unique cryptographic key pairs for each of your accounts – one public key stored on the service’s server and one private key securely stored on your device.
When you want to log in, instead of typing a password, your device uses the private key to prove your identity to the service. This process is typically triggered by your device’s built-in authentication method, such as fingerprint scan, face recognition, or PIN code.
Here’s how it works in simple terms:
When you create an account on a website, your device (like your phone) creates a special “magic key” that only works for that website
This magic key is like your personal stamp – it’s unique to you and that website
When you want to log in later, instead of typing in a password, you just use your fingerprint or face (like unlocking your phone)
Your device then uses your magic key to tell the website “Yes, this is really me!”
The beauty of passkeys lies in their simplicity and security. You don’t need to remember complex passwords, and because the private key never leaves your device, it can’t be stolen in data breaches or phishing attacks.
Single-Device vs. Syncable Passkeys
There are two main types of passkeys: single-device and syncable passkeys. Single-device passkeys are stored only on one specific device and cannot be transferred, making them ideal for dedicated work devices or high-security scenarios. Syncable passkeys, on the other hand, can be securely synchronized across multiple devices through cloud services like iCloud or Google’s password manager, offering more convenience for personal use while maintaining security.
The choice between these types depends on your security needs and usage patterns. Single-device passkeys provide maximum security but limited accessibility, while syncable passkeys offer better convenience without significantly compromising security.
Under the Hood: How Passkeys Work Their Magic 🔑
At a technical level, passkeys use public-key cryptography through the WebAuthn standard. The process consists of two phases: registration and authentication.
Passkey Registration
The purpose of this phase is to create and store a new passkey for the user. The following diagram illustrates this process:
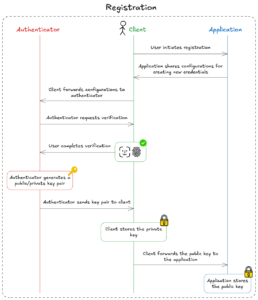
Here’s a detailed explanation of each step shown in the image:
User Starts Registration:
The process begins when a user decides to register a passkey with an application.
Application Shares Configurations:
The application sends configuration details to the client (e.g., the web browser or device) to create a new credential.
Client Sends Configurations to Authenticator:
The client passes these instructions to the authenticator (e.g., a built-in fingerprint sensor or Face scan).
Authenticator Requests Verification:
The authenticator prompts the user to verify their identity (e.g., by scanning their fingerprint or confirming presence through Face scan)
User Completes Verification:
The user successfully verifies themselves.
Public/Private Key Pair Creation and Storage:
The authenticator generates a public/private key pair
– A private key: Stays securely on the user’s device and is never shared.
– A public key: Sent back to the client.
Application Stores Public Key:
The client forwards the public key to the application, which stores it securely. This completes the registration process.
Passkey Authentication
Once a passkey is registered, it can be used to authenticate the user securely. Here’s how that process looks like:
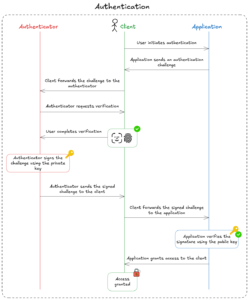
Here’s a detailed explanation of each step shown in the image:
User Initiates Authentication:
The user starts the login process.
Application Sends an Authentication Challenge:
The application generates a challenge (a random piece of data) and sends it to the client.
Client Passes the Challenge to Authenticator:
The client forwards this challenge to the authenticator.
Authenticator Requests Verification:
The authenticator asks the user to verify their identity (e.g., fingerprint or face scan).
User Completes Verification:
The user successfully verifies themselves.
Signing the Challenge:
The authenticator uses the private key to sign the challenge. This signed challenge proves the user has possession of the private key.
Client Sends Signed Challenge to Application:
The signed challenge is returned to the client, which forwards it to the application.
Application Verifies the Signature:
The application takes the signed challenge it received and compares it against the public key that was stored during the initial registration process
– Only the corresponding private key (which is securely stored on the user’s device) could have created a signature that can be verified by this public key
Access Granted:
If the signature is valid, the user is authenticated, and the application grants access.
What makes this system particularly secure is that the private key never leaves your device, and each signature is unique to that specific authentication attempt. Even if someone intercepted the communication, they couldn’t reuse it to gain access to your account.
Think of it like a super-secure digital signature: your device holds the special pen (private key) that creates signatures that only that specific website can verify (using the public key). Even if someone sees your signature, they can’t copy it because each login attempt requires a new, unique signature. This system effectively eliminates common attack vectors like password database breaches, phishing, and credential stuffing, while providing a smoother user experience.
Which Devices Support Passkeys?
Passkeys work on a broad range of devices across multiple operating systems, browsers, and applications, supporting over 90% of devices worldwide.
Operating Systems: iOS 16+, macOS 13+, Android 9+, Windows 10/11, Linux.
Supported Browsers: Safari, Chrome, Edge, Firefox, and more.
Limitations of Passkeys
While passkeys offer significant advantages over traditional passwords, they do come with some limitations and challenges:
Account Recovery
If you lose access to all your devices, account recovery can be more complex than with traditional passwords:
Recovery typically requires a backup device or going through the service provider’s account recovery process
Some services maintain backup authentication methods (like security questions or recovery emails)
Cloud synchronization services (like iCloud or Google) help mitigate this by keeping your passkeys available across devices
Device Security
If someone gains physical access to your unlocked device, they could potentially:
Access your accounts if your device’s biometric or PIN security is compromised
However, unlike passwords, passkeys can’t be easily copied or transferred to another device
You can remotely deactivate passkeys on lost devices through your account settings
Other Limitations
Not all websites and services support passkeys yet, requiring users to maintain both passwords and passkeys during the transition period
Some older devices might not support passkey authentication
Using passkeys on shared or public devices can be challenging
Despite these limitations, the security benefits of passkeys generally outweigh the drawbacks, and many of these challenges are being addressed as the technology matures.
Summary
To summarize, here are the key advantages and limitations of passkeys.
Advantages:
Immune to phishing attempts – Since passkeys use cryptographic signatures that are unique to each website, phishing attacks become ineffective
No passwords to remember or manage – Instead of memorizing complex strings, you use your device’s built-in authentication
Biometric authentication for added security – Your fingerprint or face scan provides an additional layer of security that’s hard to compromise
Synchronized across devices – Through secure cloud services, your passkeys are available on all your trusted devices
Faster login experience – No more typing long passwords or dealing with password managers—just authenticate and go
Limitations:
Account recovery can be complex if you lose access to all your devices
Physical device security is crucial – if someone gains access to your unlocked device, they could potentially access your accounts
Not all websites and services support passkeys yet
Some older devices might not be compatible
Using passkeys on shared or public devices can be challenging
Despite these limitations, the combination of security and convenience makes passkeys a compelling replacement for traditional passwords. As more services adopt this technology, we’re moving toward a future where forgotten passwords and security breaches could become a thing of the past.
Getting started with passkeys is straightforward. Here are some official resources to help you begin:
Google: Setting up and using passkeys
Apple: Using passkeys in iOS and macOS
Microsoft: Passkeys in Windows
Feel free to share this article with others who might find it helpful in understanding the future of secure authentication. Together, we can make the digital world a safer place! 🚀
Stay secure! 🔐
Extras
💡 If you’re not ready to switch to passkeys yet, consider enabling Two-Factor Authentication (2FA) on your accounts. 2FA adds an extra layer of security by requiring a second form of verification (like a code sent to your phone) in addition to your password. While not as secure as passkeys, it’s significantly better than using passwords alone.
If you’d like to learn more about the public-private key cryptography that powers passkeys, check out these excellent resources:
Cloudflare’s Guide to Public Key Cryptography – A beginner-friendly explanation of how public-private key pairs work
Asymmetric Encryption – Simply explained – Visual explanation of the concepts







